Enemy of the State with Will Smith and Gene Hackman (1998) [2:12:12]
Enemy of the State was made in 1998 and stars Gene Hackman, Lisa Bonet, Regina King, Will Smith, Jack Black, Jon Voight, and Jason Lee. This all-star cast stars in a film that performed well in its time, yet seems all the more relevant, intelligent, and interesting today. Edward Snowden didn't say too much that this movie didn't exactly say! It's pretty mind-blowing how intelligent and well-informed script-writers were.

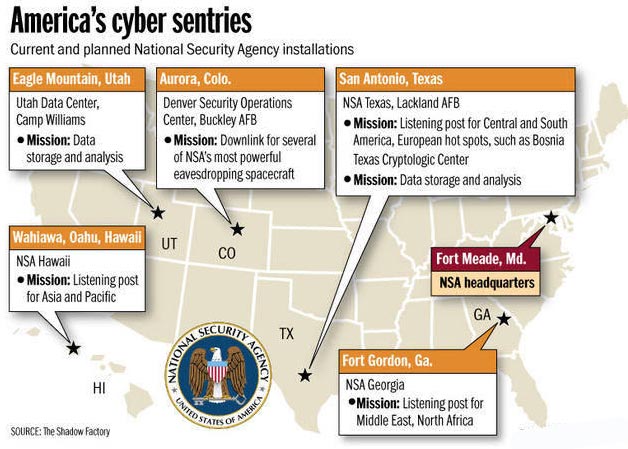
Facility
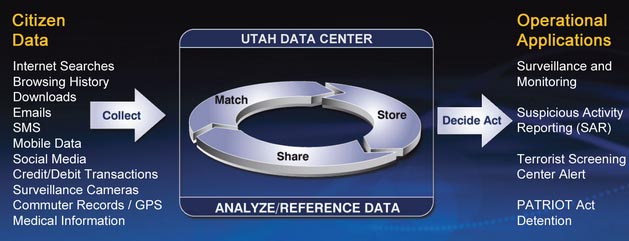
The Utah Data Center is currently under construction and is expected to open in October 2013. Our 1.5 billion-dollar one million square-foot Bluffdale / Camp Williams facility will house a 100,000 sq-ft mission critical data center. The remaining 900,000 SF will be used for technical support and administrative space. Other supporting facilities include water treatment facilities, chiller plant, power substations, vehicle inspection facility, visitor control center, and sixty diesel-fueled emergency standby generators and fuel facility for a 3-day 100% power backup capability.
Code-Breaking Supercomputer Platform
In October 2012, the U.S. Department of Energy's (DOE) Oak Ridge National Laboratory launched the Titan Supercomputer, which is capable of churning through more than 20,000 trillion calculations each second or 20 petaflops. (1 petaflop = 1 quadrillion instructions per second).
Data Storage Capacity
The storage capacity of the Utah Data Center will be measured in "zettabytes". What exactly is a zettabyte? There are a thousand gigabytes in a terabyte; a thousand terabytes in a petabyte; a thousand petabytes in an exabyte; and a thousand exabytes in a zettabyte.
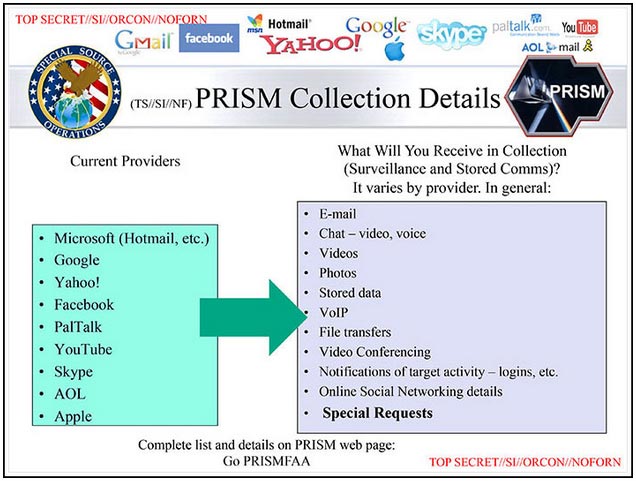
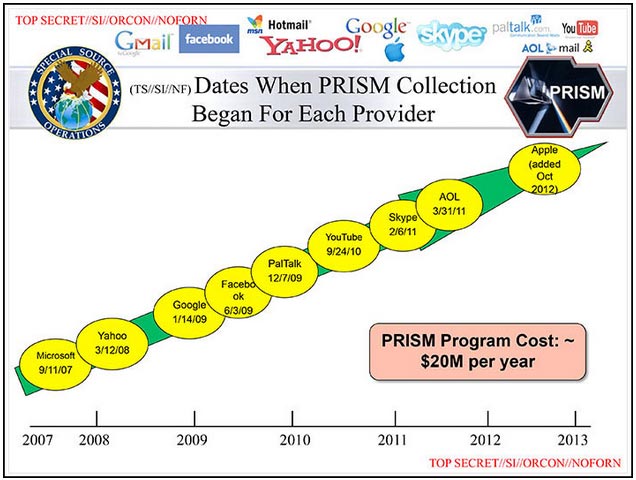
PRISM Data Collection Program:
Established in 2007, the PRISM program, our analysts can extract information directly from the servers of nine major American internet companies: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple. This important partnership gives us direct access to audio, video, photographs, e-mails, documents and connection logs for each of these systems.
The Utah Data Center is currently under construction and is expected to open in October 2013. Our 1.5 billion-dollar one million square-foot Bluffdale / Camp Williams facility will house a 100,000 sq-ft mission critical data center. The remaining 900,000 SF will be used for technical support and administrative space. Other supporting facilities include water treatment facilities, chiller plant, power substations, vehicle inspection facility, visitor control center, and sixty diesel-fueled emergency standby generators and fuel facility for a 3-day 100% power backup capability.
Code-Breaking Supercomputer Platform
In October 2012, the U.S. Department of Energy's (DOE) Oak Ridge National Laboratory launched the Titan Supercomputer, which is capable of churning through more than 20,000 trillion calculations each second or 20 petaflops. (1 petaflop = 1 quadrillion instructions per second).
Data Storage Capacity
The storage capacity of the Utah Data Center will be measured in "zettabytes". What exactly is a zettabyte? There are a thousand gigabytes in a terabyte; a thousand terabytes in a petabyte; a thousand petabytes in an exabyte; and a thousand exabytes in a zettabyte.
PRISM Data Collection Program:
Established in 2007, the PRISM program, our analysts can extract information directly from the servers of nine major American internet companies: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple. This important partnership gives us direct access to audio, video, photographs, e-mails, documents and connection logs for each of these systems.
Who
Where
What
When
NSA News | Nationial Security State Programs
ThinThreadThinThread is the name of a project that the United States National Security Agency (NSA) pursued during the 1990s, according to a May 17, 2006 article in The Baltimore Sun. The program involved wiretapping and sophisticated analysis of the resulting data, but according to the article, the program was discontinued three weeks before the September 11, 2001 attacks due to the changes in priorities and the consolidation of U.S. intelligence authority. The "change in priority" consisted of the decision made by the director of NSA General Michael V. Hayden to go with a concept called Trailblazer, despite the fact that ThinThread was a working prototype that protected the privacy of U.S. citizens.
ThinThread was dismissed and replaced by the Trailblazer Project, which lacked the privacy protections. A consortium led by Science Applications International Corporation was awarded a $280 million contract to develop Trailblazer in 2002.
ThinThread at Wikipedia
NSA - Trailblazer
Trailblazer was a United States National Security Agency (NSA) program intended to develop a capability to analyze data carried on communications networks like the Internet. It was intended to track entities using communication methods such as cell phones and e-mail. It ran over budget, failed to accomplish critical goals, and was cancelled.
NSA whistleblowers J. Kirk Wiebe, William Binney, Ed Loomis, and House Permanent Select Committee on Intelligence staffer Diane Roark complained to the Department of Defense's Inspector General (IG) about waste, fraud, and abuse in the program, and the fact that a successful operating prototype existed, ThinThread, but was ignored when the Trailblazer program was launched.
Trailblazer Project - Wikipedia
NSA - Turbulence
Turbulence is a National Security Agency (NSA) Information Technology project started circa 2005. It was developed in small, inexpensive "test" pieces rather than one grand plan like its failed predecessor, the Trailblazer Project. It also includes offensive cyber-warfare capabilities, like injecting malware into remote computers. Congress criticized Turbulence in 2007 for having similar bureaucratic problems as Trailblazer.
According to Siobhan Gorman in a 2007 Baltimore Sun article, "The conclusion in Congress, two former government officials said, was that Turbulence was over budget, not delivering and poorly led, and that there was little or no strategy to pull it all together."
Turbulence (NSA) - Wikipedia
NSA - Stellar Wind
Stellar Wind was the open secret code name for four surveillance programs by the United States National Security Agency (NSA) during the presidency of George W. Bush and revealed by Thomas Tamm to The New York Times reporters James Risen and Eric Lichtblau. The operation was approved by President George W. Bush shortly after the September 11 attacks in 2001. Stellar Wind was succeeded during the presidency of Barack Obama by four major lines of intelligence collection in the territorial United States, together capable of spanning the full range of modern telecommunications.
The program's activities involved data mining of a large database of the communications of American citizens, including e-mail communications, phone conversations, financial transactions, and Internet activity. William Binney, a retired Technical Leader with the NSA, discussed some of the architectural and operational elements of the program at the 2012 Chaos Communication Congress.
Stellar Wind - Wikipedia
NSA - Total Information Awareness (Poindexter)
 The Information Awareness Office (IAO) was established by the Defense
Advanced Research Projects Agency (DARPA) in January 2002 to bring together
several DARPA projects focused on applying surveillance and information
technology to track and monitor terrorists and other asymmetric threats to
U.S. national security, by achieving Total Information Awareness (TIA).
The Information Awareness Office (IAO) was established by the Defense
Advanced Research Projects Agency (DARPA) in January 2002 to bring together
several DARPA projects focused on applying surveillance and information
technology to track and monitor terrorists and other asymmetric threats to
U.S. national security, by achieving Total Information Awareness (TIA).This would be achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. This information would then be analyzed to look for suspicious activities, connections between individuals, and "threats". Additionally, the program included funding for biometric surveillance technologies that could identify and track individuals using surveillance cameras, and other methods.
Information Awareness Office - Wikipedia